Wireless
No edit summary |
No edit summary |
||
| (147 intermediate revisions by 4 users not shown) | |||
| Line 1: | Line 1: | ||
[[Category:IT]] | |||
[[General-network|Network overview]] | |||
[[Wireless-New|Wireless config page]] | |||
=== Connecting === | |||
==== Windows XP ==== | |||
Use Hyperterminal to connect to a unit: | |||
-> Use 9600 baud, no parity, 1 stop bit, and disable hardware flow control. | |||
==== OSX/Linux ==== | |||
There should be a USB/Serial cable in the box. Clive will also have one in his bag of stuff. But if you lose his, it will be painful ... | |||
Find the port number in terminal: | |||
<nowiki>$ ls -ltr /dev/*usb* | |||
crw-rw-rw- 1 root wheel 21, 2 7 Apr 16:33 /dev/tty.usbserial-AH0668GD | |||
crw-rw-rw- 1 root wheel 21, 3 7 Apr 16:33 /dev/cu.usbserial-AH0668GD</nowiki> | |||
or | |||
<nowiki>matt@merple:~> ls -ltr /dev/ | grep -i usb | |||
crw-rw---- 1 root dialout 188, 0 Sep 13 21:11 /dev/ttyUSB0 | |||
matt@merple:~> </nowiki> | |||
You can use screen to connect: | |||
<nowiki>$ screen /dev/tty.usbserial-AH0668GD 9600</nowiki> | |||
Personally, Clive hates using screen, so has downloaded and installed [https://github.com/lime45/serial.git a small cli serial emulator]. If you're on a machine it's been installed on, having found the port you want, you connect using: | |||
<nowiki>serial /dev/tty.usbserial-AH0668GD 9600</nowiki> | |||
==== Log in ==== | |||
If you've got things right, then if you have the cable plugged in when you turn a wireless | If you've got things right, then if you have the cable plugged in when you turn a wireless | ||
base-unit on, you should see boot-time messages start to scroll past for about a minute after | base-unit on, you should see boot-time messages start to scroll past for about a minute after | ||
| Line 72: | Line 42: | ||
<TAB> will auto-complete unambiguous partial commands. | <TAB> will auto-complete unambiguous partial commands. | ||
== Configuring units == | |||
==== Common ==== | |||
* Enter admin mode | |||
** Gain privileged access: | |||
<nowiki>enable</nowiki> | |||
* Enter config mode. | |||
** Enter (configuration) context: | |||
<nowiki>configure terminal</nowiki> | |||
<nowiki>show dot11 network-map</nowiki> | |||
* Show live configuration: | |||
<nowiki>show running-config</nowiki> | |||
* Commit live configuration as the new default: | |||
<nowiki>write memory</nowiki> | |||
* Show neighbouring Cisco equipment: | |||
<nowiki>show cdp neighbors [detail]</nowiki> | |||
* Show interface status: | |||
<nowiki>sh ip interface brief</nowiki> | |||
* Get an idea of your network map: | |||
<nowiki>bridge-e#sh dot11 associations</nowiki> | |||
== Updating the operating system --- Here be dragons == | |||
Some problems Clive has been having with some of the devices have been resolved by updating to a more recent version of IOS. (Yes, Cisco also call their OS IOS. In fairness, they were there first: [https://blogs.cisco.com/news/cisco_and_apple_agreement_on_ios_trademark “Cisco has agreed to license the iOS trademark to Apple for use as the name of Apple’s operating system for iPhone, iPod touch and iPad. The license is for use of the trademark only and not for any technology.”]) | |||
There should be a running tftp server on favog. It should even have one or more IOS images on it. It'll look like this: | |||
<nowiki> ls -ls /srv/tftpboot/ | |||
total 5284 | |||
5284 -rw-r--r-- 1 tftp tftp 5408256 Apr 23 19:41 c1310-k9w7-mx.124-10b.JA1.tar</nowiki> | |||
=== Steps === | |||
Simple in principle: | |||
# Find an equivalent piece of hardware that is working and has the feature | |||
# Get both devices on the network, use an ethernet cable for preference | |||
# Upload its current image, if it's not already there | |||
# Download it on the 'broken' one | |||
==== Upload an image ==== | |||
First, find out what image you have. It'll be the directory with long name starting with your hardware's part number, eg: | |||
<nowiki>bridge-e#sh flash | |||
Directory of flash:/ | |||
2 -rwx 2072 Mar 1 2002 00:11:18 +00:00 private-multiple-fs | |||
3 -rwx 1261 Mar 1 2002 00:11:18 +00:00 config.txt | |||
4 drwx 256 Jan 1 1970 00:06:24 +00:00 c1310-k9w7-mx.124-10b.JA1 | |||
153 -rwx 70 Mar 1 2002 00:02:33 +00:00 env_vars | |||
155 -rwx 5 Mar 1 2002 00:11:18 +00:00 private-config | |||
7741440 bytes total (2395648 bytes free)</nowiki> | |||
In this case, '''c1310-k9w7-mx.124-10b.JA1''' | |||
Copying it is actually fairly easy: | |||
<nowiki>bridge-e#archive upload-sw tftp://10.0.0.18/[the directory name from above].tar</nowiki> | |||
=== Download an image ==== | |||
Again, relatively easy: | |||
<nowiki>bridge-f#archive download-sw tftp://10.0.0.18/[the directory name from above].tar</nowiki> | |||
You'll see something along the lines of: | |||
<nowiki>examining image... | |||
Loading c1310-k9w7-mx.124-10b.JA1.tar from 192.168.0.20 (via BVI1): ! | |||
extracting info (275 bytes)!!!!!!!!!!!!!!!!! | |||
[OK - 5408256 bytes] | |||
Image info: | |||
Version Suffix: k9w7-.124-10b.JA1 | |||
Image Name: c1310-k9w7-mx.124-10b.JA1 | |||
Version Directory: c1310-k9w7-mx.124-10b.JA1 | |||
Ios Image Size: 4669952 | |||
Total Image Size: 5407232 | |||
Image Feature: UNKNOWN | |||
Image Family: C1310 | |||
Wireless Switch Management Version: 1.0</nowiki> | |||
followed by a lot of progress information which may well include wiping the original image out. | |||
Once this is done, restart it. And hope that you've not bricked it ... | |||
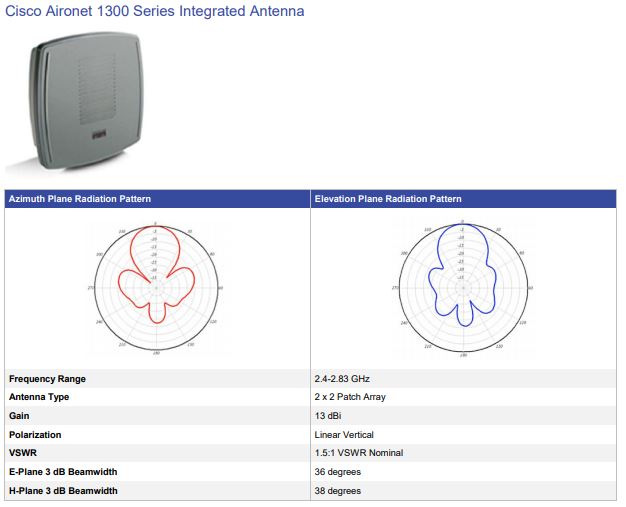
==Radiation Patterns== | |||
[[File:Cisco1300.JPG]] | |||
Latest revision as of 15:06, 11 September 2025
Connecting
Windows XP
Use Hyperterminal to connect to a unit:
-> Use 9600 baud, no parity, 1 stop bit, and disable hardware flow control.
OSX/Linux
There should be a USB/Serial cable in the box. Clive will also have one in his bag of stuff. But if you lose his, it will be painful ...
Find the port number in terminal:
$ ls -ltr /dev/*usb* crw-rw-rw- 1 root wheel 21, 2 7 Apr 16:33 /dev/tty.usbserial-AH0668GD crw-rw-rw- 1 root wheel 21, 3 7 Apr 16:33 /dev/cu.usbserial-AH0668GD
or
matt@merple:~> ls -ltr /dev/ | grep -i usb crw-rw---- 1 root dialout 188, 0 Sep 13 21:11 /dev/ttyUSB0 matt@merple:~>
You can use screen to connect:
$ screen /dev/tty.usbserial-AH0668GD 9600
Personally, Clive hates using screen, so has downloaded and installed a small cli serial emulator. If you're on a machine it's been installed on, having found the port you want, you connect using:
serial /dev/tty.usbserial-AH0668GD 9600
Log in
If you've got things right, then if you have the cable plugged in when you turn a wireless base-unit on, you should see boot-time messages start to scroll past for about a minute after power-on.
Press <ENTER> when prompted to bring up control menu.
Prompt is displayed as: ap> -- or, if the device has been given a different hostname, either manually or via DHCP, then it will appear as: hostname>
Pressing '?' will display a list of commands. <TAB> will auto-complete unambiguous partial commands.
Configuring units
Common
- Enter admin mode
- Gain privileged access:
enable
- Enter config mode.
- Enter (configuration) context:
configure terminal
show dot11 network-map
- Show live configuration:
show running-config
- Commit live configuration as the new default:
write memory
- Show neighbouring Cisco equipment:
show cdp neighbors [detail]
- Show interface status:
sh ip interface brief
- Get an idea of your network map:
bridge-e#sh dot11 associations
Updating the operating system --- Here be dragons
Some problems Clive has been having with some of the devices have been resolved by updating to a more recent version of IOS. (Yes, Cisco also call their OS IOS. In fairness, they were there first: “Cisco has agreed to license the iOS trademark to Apple for use as the name of Apple’s operating system for iPhone, iPod touch and iPad. The license is for use of the trademark only and not for any technology.”)
There should be a running tftp server on favog. It should even have one or more IOS images on it. It'll look like this:
ls -ls /srv/tftpboot/ total 5284 5284 -rw-r--r-- 1 tftp tftp 5408256 Apr 23 19:41 c1310-k9w7-mx.124-10b.JA1.tar
Steps
Simple in principle:
- Find an equivalent piece of hardware that is working and has the feature
- Get both devices on the network, use an ethernet cable for preference
- Upload its current image, if it's not already there
- Download it on the 'broken' one
Upload an image
First, find out what image you have. It'll be the directory with long name starting with your hardware's part number, eg:
bridge-e#sh flash
Directory of flash:/
2 -rwx 2072 Mar 1 2002 00:11:18 +00:00 private-multiple-fs
3 -rwx 1261 Mar 1 2002 00:11:18 +00:00 config.txt
4 drwx 256 Jan 1 1970 00:06:24 +00:00 c1310-k9w7-mx.124-10b.JA1
153 -rwx 70 Mar 1 2002 00:02:33 +00:00 env_vars
155 -rwx 5 Mar 1 2002 00:11:18 +00:00 private-config
7741440 bytes total (2395648 bytes free)
In this case, c1310-k9w7-mx.124-10b.JA1
Copying it is actually fairly easy:
bridge-e#archive upload-sw tftp://10.0.0.18/[the directory name from above].tar
Download an image =
Again, relatively easy:
bridge-f#archive download-sw tftp://10.0.0.18/[the directory name from above].tar
You'll see something along the lines of:
examining image...
Loading c1310-k9w7-mx.124-10b.JA1.tar from 192.168.0.20 (via BVI1): !
extracting info (275 bytes)!!!!!!!!!!!!!!!!!
[OK - 5408256 bytes]
Image info:
Version Suffix: k9w7-.124-10b.JA1
Image Name: c1310-k9w7-mx.124-10b.JA1
Version Directory: c1310-k9w7-mx.124-10b.JA1
Ios Image Size: 4669952
Total Image Size: 5407232
Image Feature: UNKNOWN
Image Family: C1310
Wireless Switch Management Version: 1.0
followed by a lot of progress information which may well include wiping the original image out.
Once this is done, restart it. And hope that you've not bricked it ...